Consenter risk assessment

Why is the Consenter risk assessment trustworthy?
The Consenter risk assessment corresponds to the data protection risk assessment pursuant to Articles 25 and 35 of the GDPR. The methodology of this risk assessment is based on a research and development process spanning more than 10 years within and between numerous European research institutions and data protection authorities.
Data protection risk assessment involves examining various factors to determine which fundamental rights of the users of your service are at risk when you process their personal data. To this end, we examine the specific processing procedure, amongst other aspects, with regard to the type of data, the purposes and nature of its processing, the context of its collection, and the social roles of the actors involved.
Over the last decade, we have conducted numerous research projects to determine which typical processing procedures pose which fundamental rights risks, how these risks can best be controlled, and how they can be communicated most clearly to laypeople so that they can adapt to them in the best possible way.
To make this risk assessment as effective and efficient as possible for service providers, such as you as a website operators, we have automated the risk assessment process. To this aim, we examine each individual third-party tool and its configuration options with regard to the factors mentioned above.
On this basis, you can now configure the tools according to your needs and observe the effects of your respective configuration on the risk-benefit ratio in near real time, which is then communicated to your end users. This feedback loop gives you immediate control over the risks these tools pose to your end users, your own compliance risk and, ultimately, your consent rate.
Third party (service) provider
Technologies from third party service providers (TPPs), such as Matomo or Google Analytics, are essential for successfully operating, maintaining, and improving websites. Different tools carry varying risks based on factors like the provider's location and the data they process by default for specific purposes. TPPs thus play a key role in determining—and potentially reducing—risks to users' fundamental rights.
Common alternative terms include third party providers, vendors, external providers, technology providers, and external vendors. For simplicity, we refer to them as third party providers or TPPs
How to decrease the risks to increase your consent rate?
As promised, Consenter Manager gives you complete control over the risks associated, especially, with integrating third-party tools for your users and, consequently, your legal compliance. For this purpose, we provide you with specific configuration guides for third party technology providers (TPPs). In these guides, we show you
- on the one hand, how to configure the respective third-party technology so that you can find the optimal balance between the functionalities that the tool offers and the data protection risk that these functionalities pose to your end users; and
- on the other hand, how to configure your consent banner in your Consenter Manager so that you not only comply with your information duties, but can also advertise the increased level of data protection on your website to your users (see above under 'How to create a consent banner with Consenter').
For this purpose, each TPP guide contains a table that typically lists four different risk configurations: lowest risk, low risk, high risk, highest risk. These risk configurations run in columns across several rows from top to bottom.
What is the TPP configuration guide for?
With these risk configurations, we help you gain in advance an overview of the potential overall risk when configuring the third-party technology.
Of course, if you represent, in a second step, your TPP configuration in the Consenter Manager accordingly, we will automatically map the associated risk with each singular entry. The Risk Benefit Wheel on the left-hand side of Consenter Manager also shows you the respective interim risk in real time.
However, many of the risks associated with the individual settings must first accumulate until they reach a certain threshold, which is indicated by the Risk Benefit Wheel. The TPP guides will therefore help you to plan ahead, according to our four risk configurations.

Recommendation
We recommend choosing the low-risk setup because it affects overall privacy impact shown to your users in the Consenter banner, which influences your consent rates.
However, every website is different. Lower-risk setups often offer fewer features or require more manual work, while higher-risk setups unlock more functionality (see above "How to create a consent banner with Consenter?"). This guide simply helps you understand that trade-off so you can choose the configuration that best fits your needs.
If you follow one of our suggested risk configurations, you can now transfer the configuration suggestions from our guide line by line into the settings of the third-party technology and then into the Consent Manager. (As mentioned, you can deviate from the recommendations at any time; they are only intended to provide you with a forward-looking overview.)
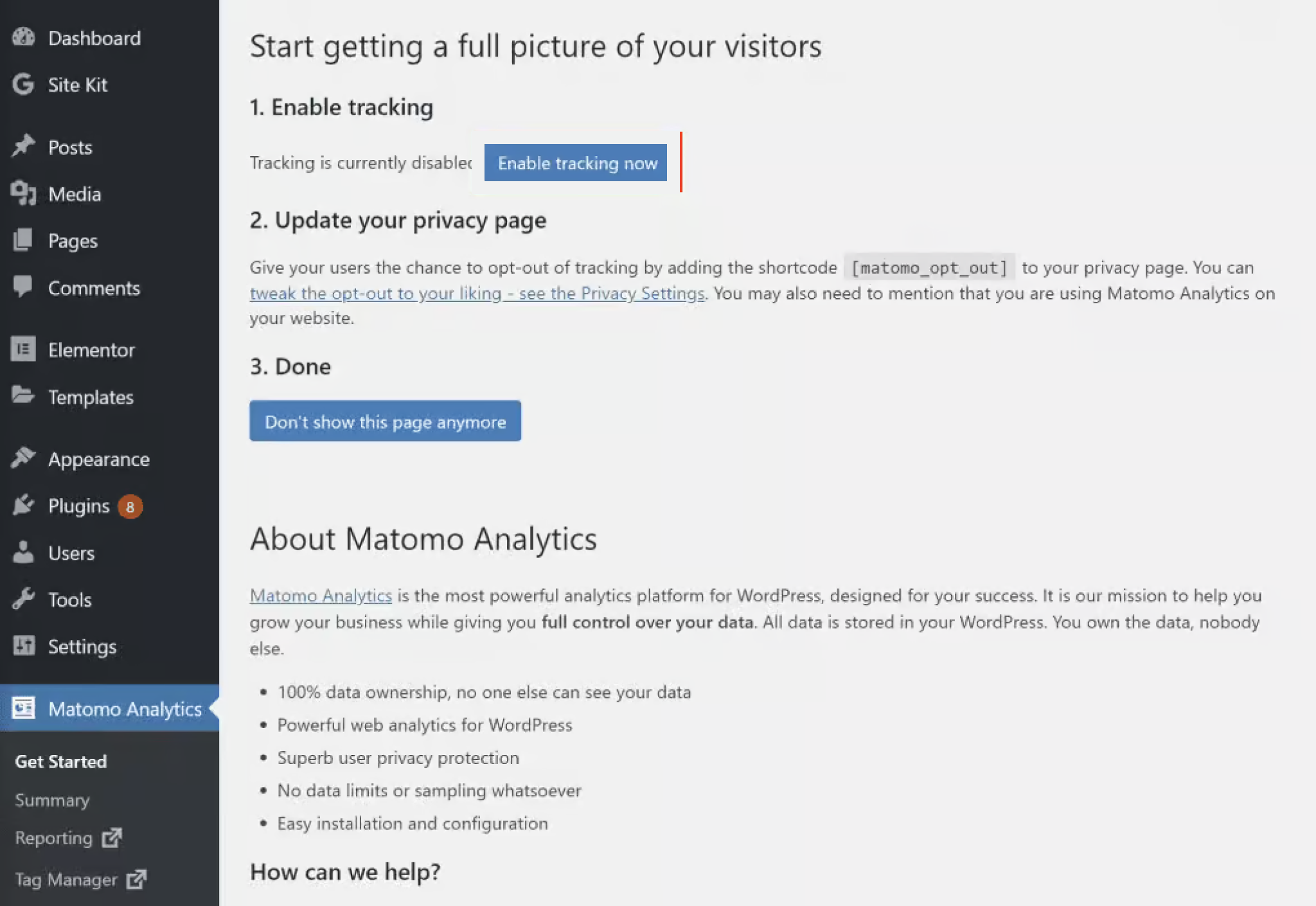
Example of Matomo Analytics settings
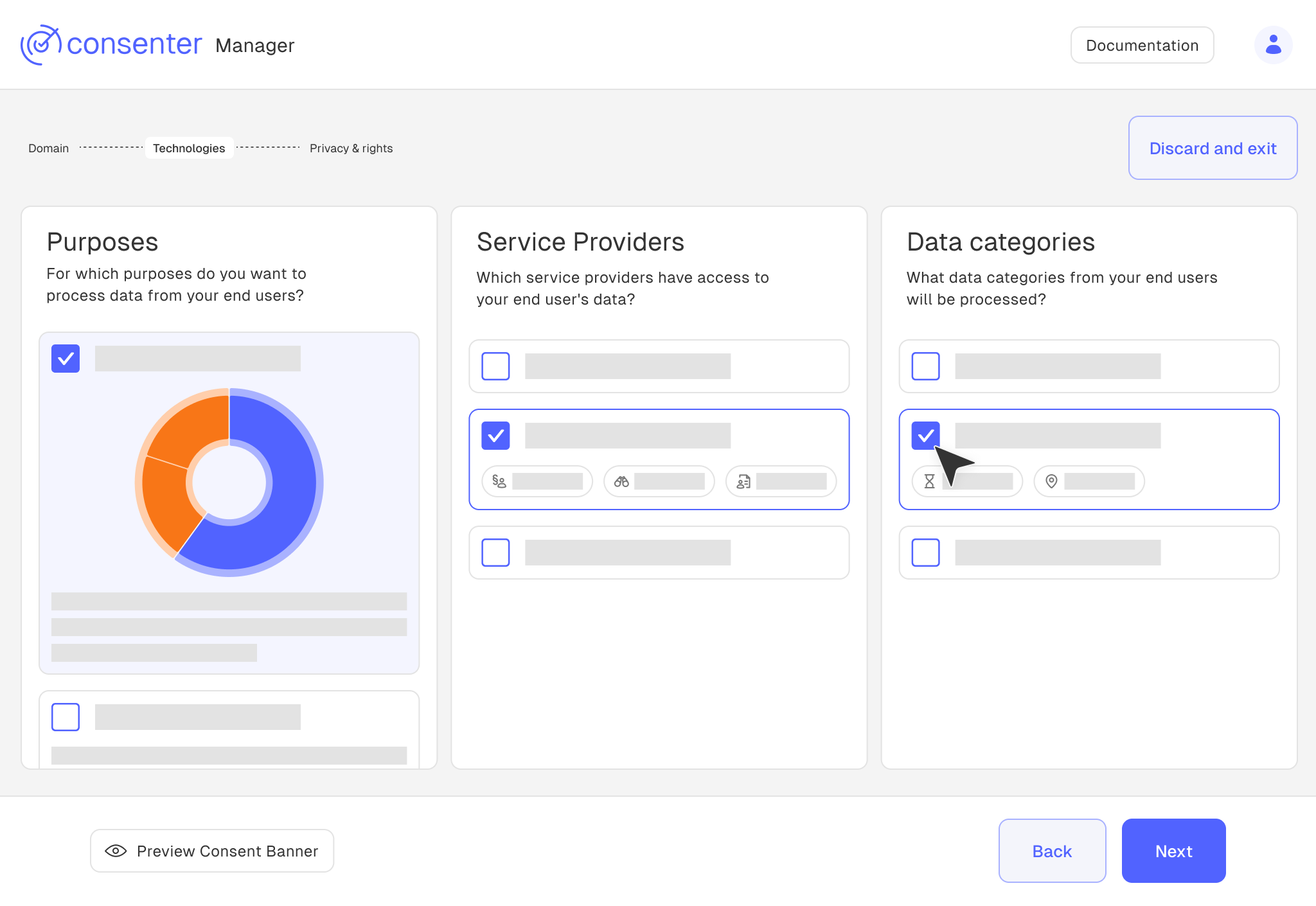
Accordingly, settings in Consenter Manager
How does Consenter communicate the risk to you and your users?
As mentioned above, how you configure the third-party provider technology has an impact on your users – and your consent rate. In Consenter Manager, you can therefore view an overview of the final risk-benefit ratio at the end of each configuration process for a specific purpose.
Most websites have a fairly mediocre to poor level of data protection. This is not usually the fault of the website providers, but is generally due to a lack of knowledge. For this reason, we also assume a fairly mediocre to poor level of data protection in the consent agent, where we explain to users the risks and benefits typically associated with the various processing purposes in a general way. If you configure your third-party tool better than most other website providers do, we can communicate this to your website visitors. This increases their trust and thus tends to increase your consent rate.
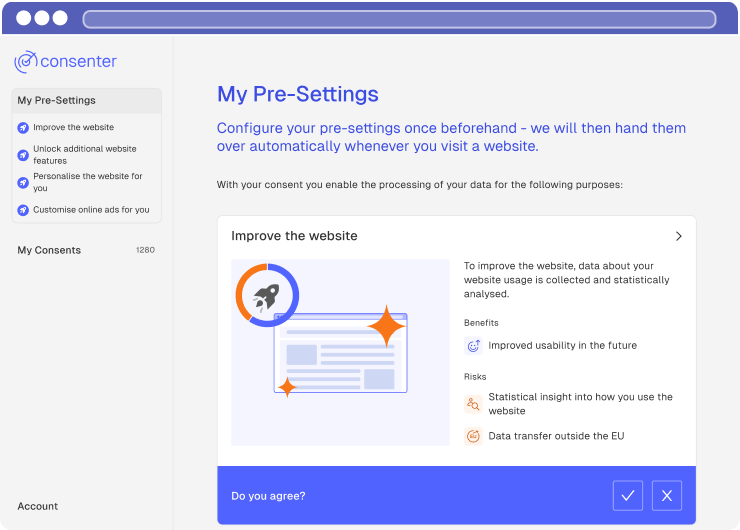
Consent Agent showing poor level of protection in general
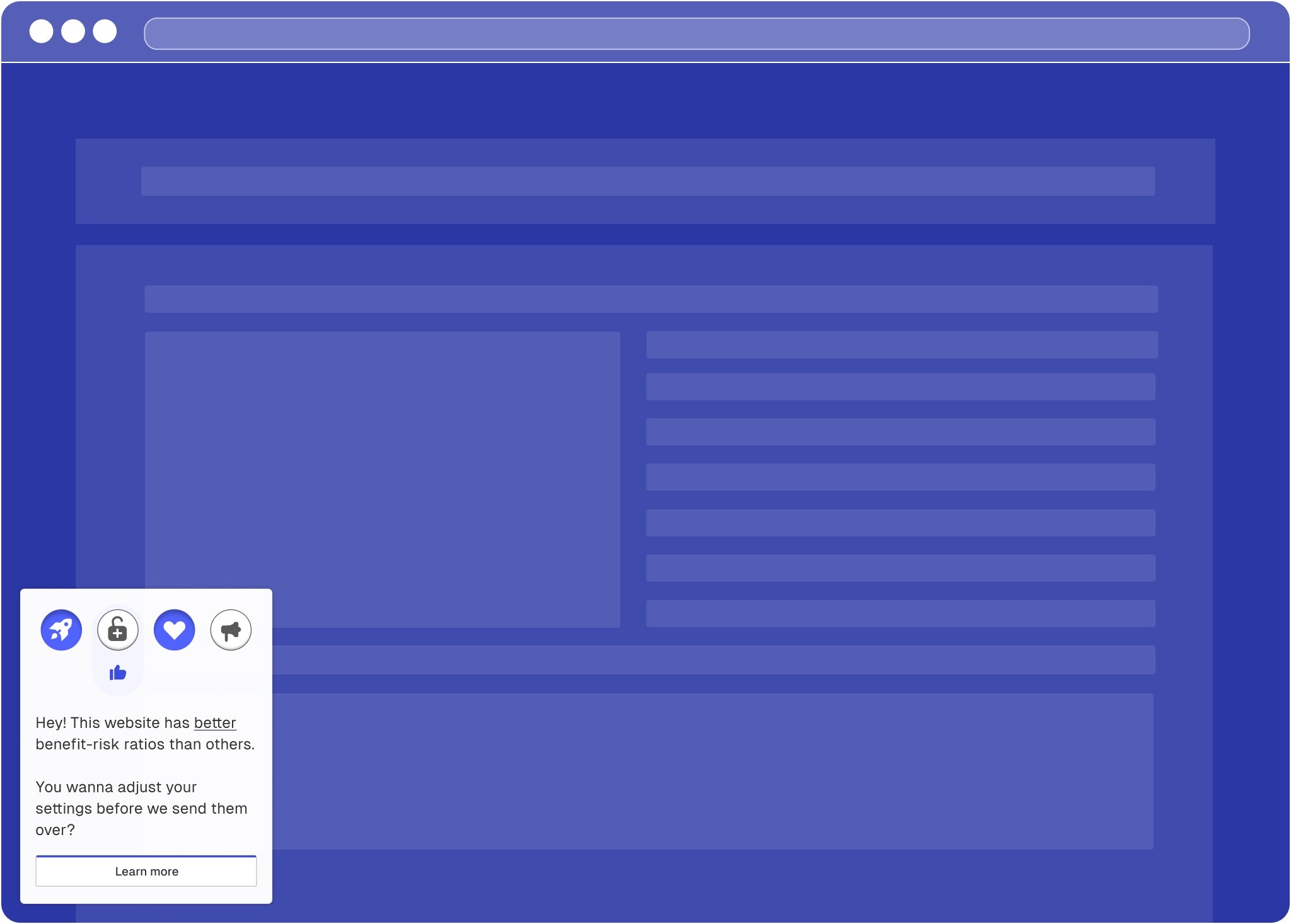
Specific risk-benefit ratio on handover notice (often better)
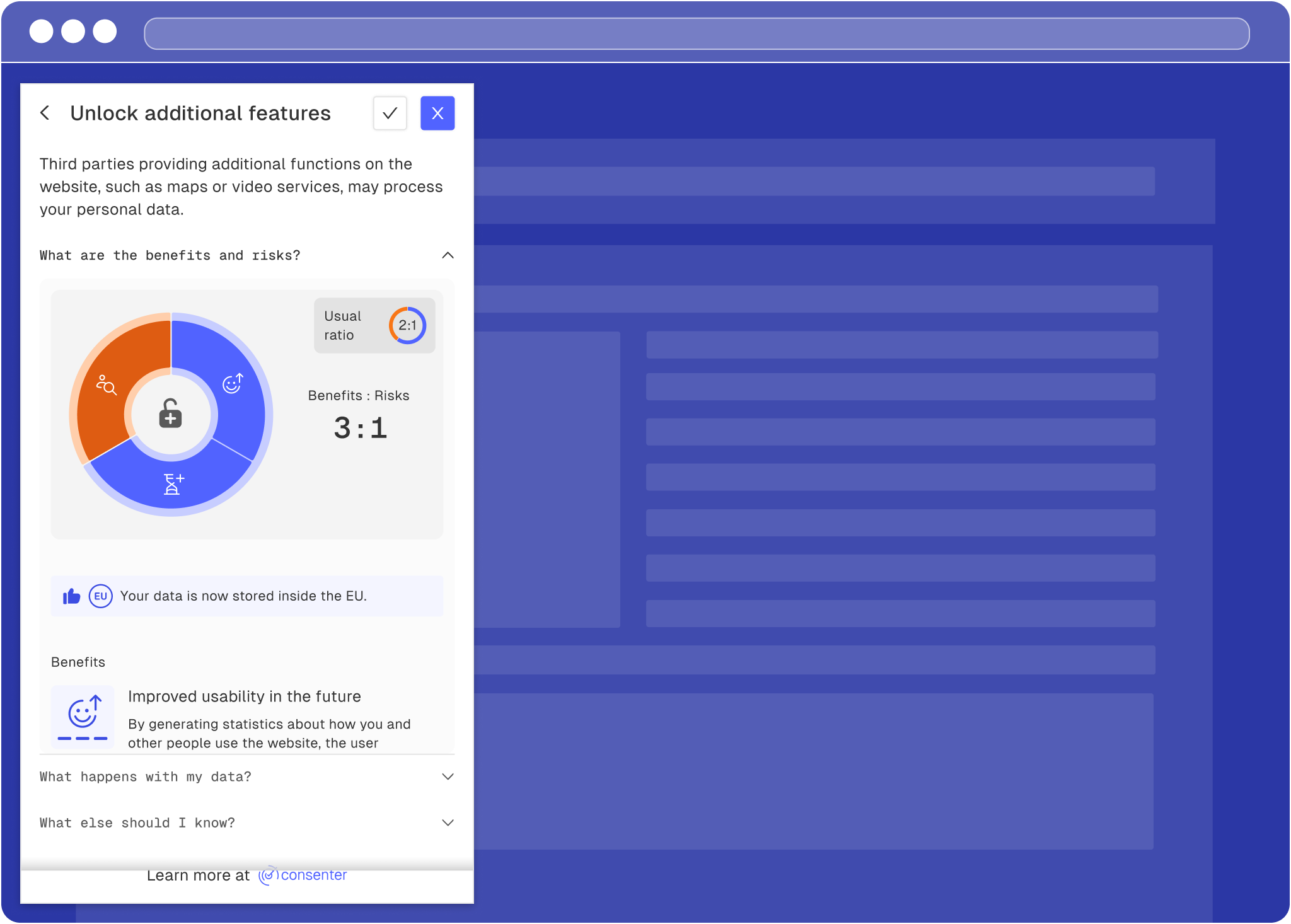
Specific risk-benefit ratio on consent banner (often better)
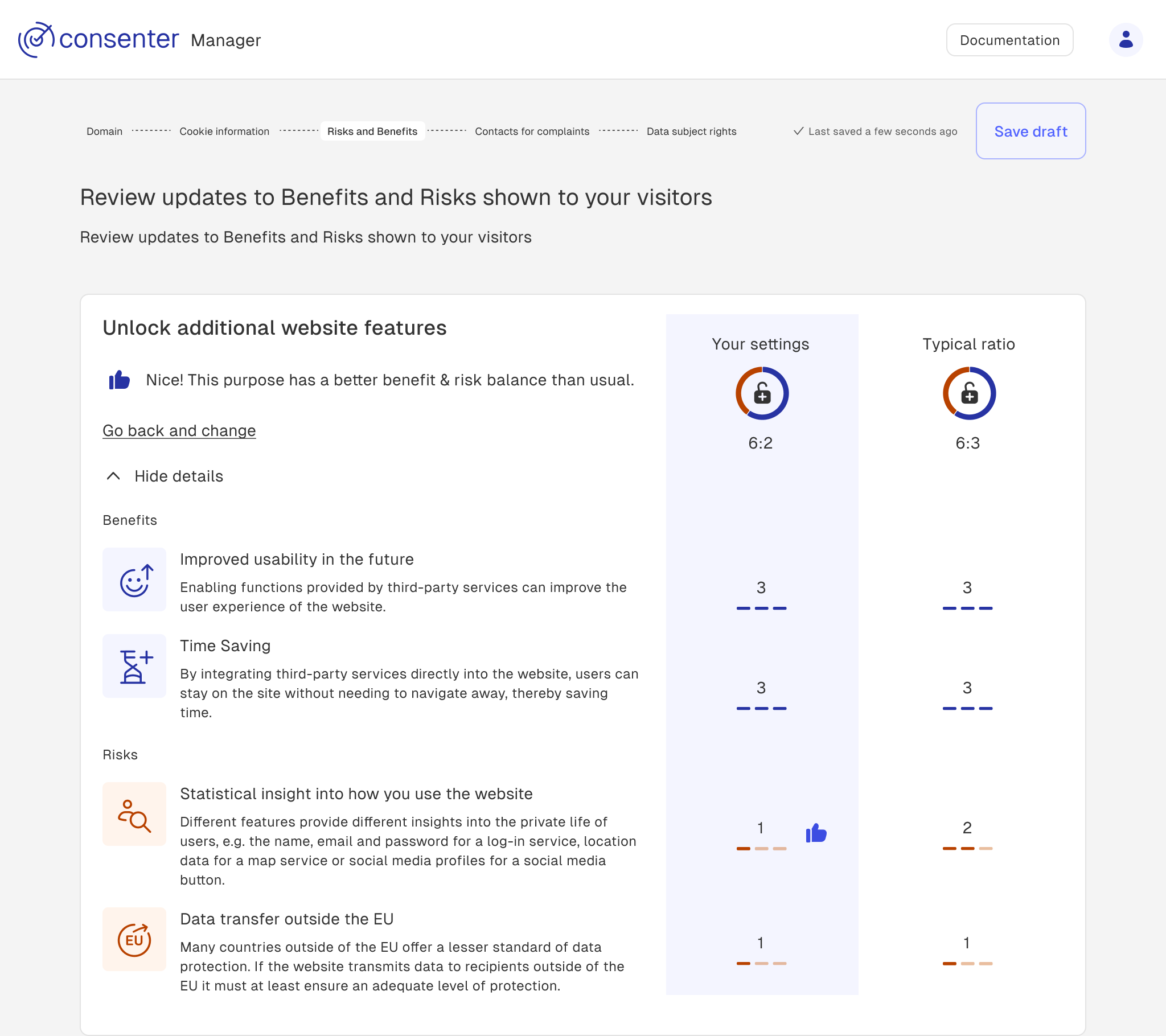
Better risk-benefit ratio than usual
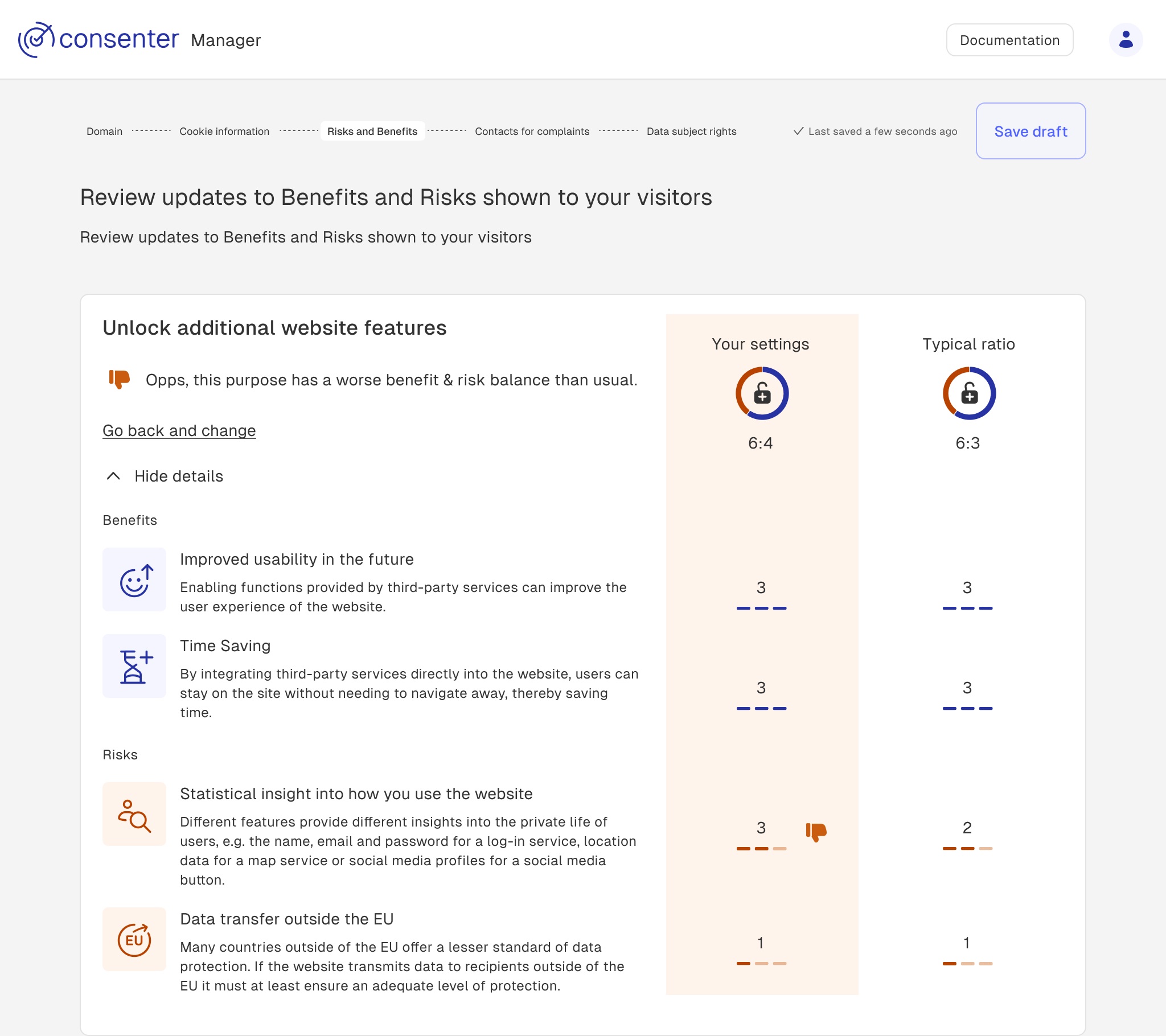
Worse risk-benefit ratio than usual
Depending on whether your users had already made a decision for or against giving their consent, they will now be shown the new risk-benefit ratio when they visit your website again and will have the opportunity to reconsider their previous decision.
How does the risk assessment work in detail?
When configuring the consent banner in the Consenter customer panel, each change you make directly affects the associated fundamental rights risk for your website visitors. This impact is visualised in the risk-benefit wheel displayed in the left-hand column of the Consenter Manager.

Consenter Manager
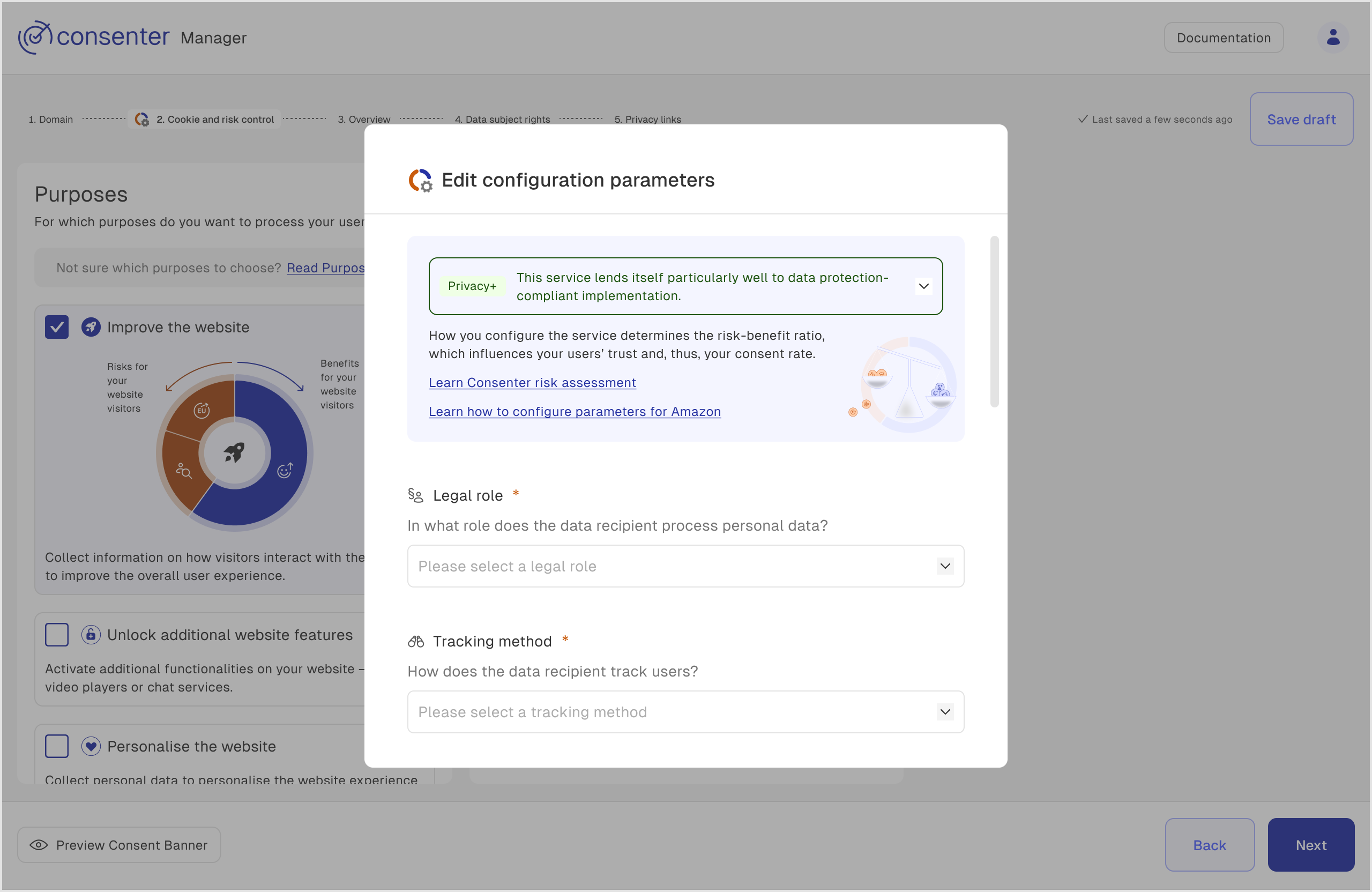

What influences the risk score
The following parameters determine the risk calculation and contribute to the overall risk score of your specific configuration (see below for a more detailed listing):
- Tracking methods used, if any
- Categories of personal data processed
- Data storage duration
- Data storage location
- Legal roles of third-party providers involved in processing
- Use of personalisation and the type of personalisation model applied
Each selection option within these parameters is assigned a weighted score based on its potential impact on fundamental rights such as privacy and autonomy, derived from our research results.
How configuration changes affect the score
As a result, every combination of third-party providers, data categories, tracking technologies, and other configuration settings produces a unique risk score. This score is reflected in the risk-benefit wheel and transparently communicated to your website visitors.
If your configuration achieves a more favourable risk-benefit ratio than the default settings, your website visitors will be informed of this improvement, which may positively influence their willingness to consent to data processing for a specified purpose.
Should you later adopt more privacy-friendly technologies, these changes will automatically update the risk-benefit wheel. This update enables you to re-engage visitors and ask for consent again based on the improved configuration.
Specific risk parameters:
Each option in the right-hand column carries an individual score that represents its relevance to fundamental rights like privacy.
| Storage location | EU |
|---|---|
| Adequacy decision | |
| Appropriate safeguards | |
| Risk reduction per additional safeguard | |
| No legal basis | |
| Data category | Aggregated site statistics |
| Non-precise location data | |
| Device characteristics | |
| IP-Adress anonymised | |
| IP address | |
| Privacy choices | |
| Authentication-derived identifiers | |
| Browsing and interaction data | |
| Device identifiers | |
| User-provided data | |
| Precise location data | |
| Probabilistic identifiers | |
| e-commerce Activity | |
| Direct identifiers | |
| Social media interaction data | |
| Special categories Art. 9 GDPR | |
| Users' profiles | |
| Storage duration | < 1 year |
| > 1 year | |
| Legal role | Self-hosted |
| Processor | |
| Joint Controller | |
| Controller | |
| Personalisation | No personalisation |
| Group based (properties) | |
| Group based (behaviour) | |
| Profile based | |
| Tracking method | No tracking |
| First party tracking / single session cookieless | |
| First party tracking / cross session | |
| First party / Cross session tracking | |
| Third Party (Cross website/single session) tracking | |
| Third Party (Cross website/cross Session) tracking | |
| Third Party (Cross website/cross Session/cross device) tracking |
How is this guide?
Last updated on